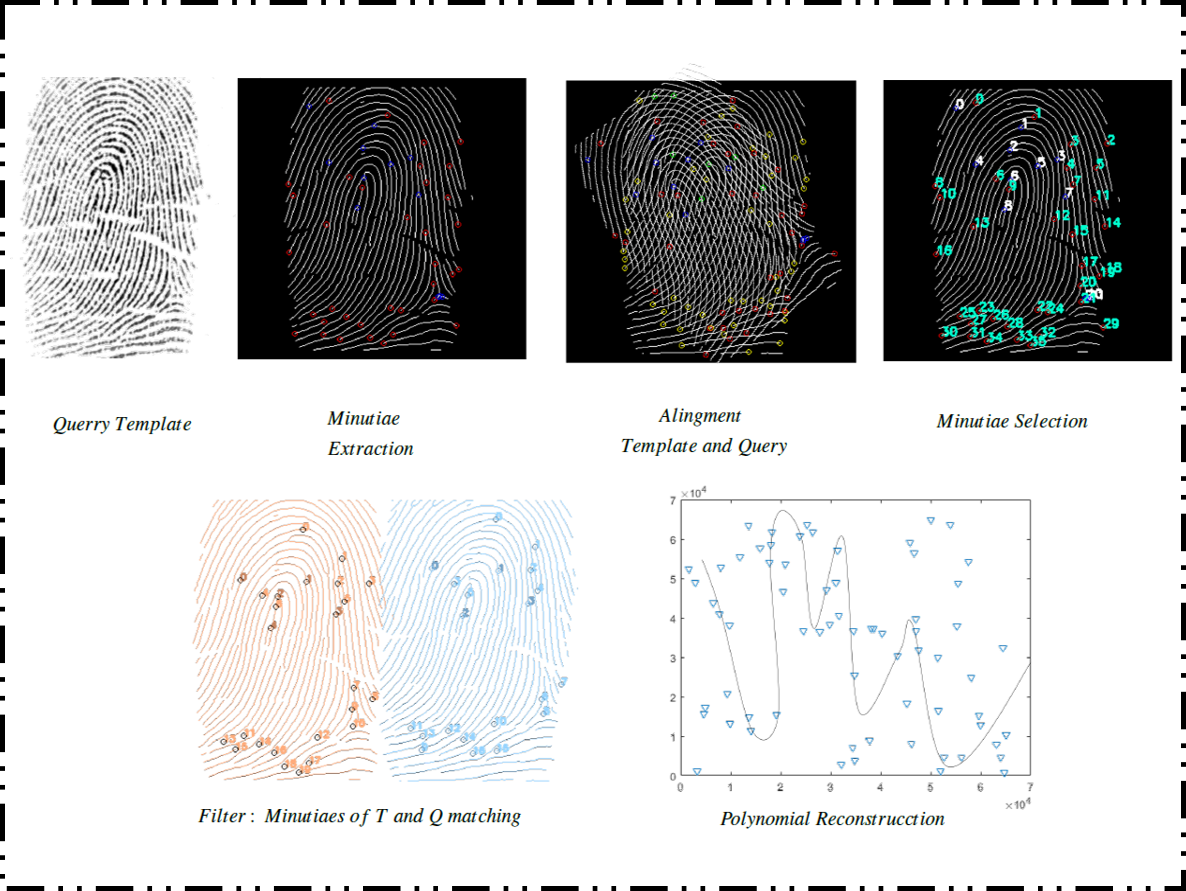
Throughout this social service program, an extensive bibliographic review of the functioning of biometric systems used in conjunction with cryptographic systems to protect information was carried out. Specifically, we focused on the operation of the Fuzzy Vault scheme based on Fingerprint; we studied the original scheme proposal as well as the existing implementations.
Subsequently, the study was redirected towards the identified attacks to which the scheme may be vulnerable. Diagrams, reports and other didactic resources were constructed from the attacks studied to improve their understanding and study. Within the set of attacks whose diagrams were obtained, a subset was chosen from which a simulation was built by programming them. This was done with the objective of attacking vaults generated with a Fuzzy Fingerprint-based Vault system that was adapted for the simulations of the attacks.
A data analysis of the results obtained in the experiments carried out with the attack simulations was performed. In addition, we experimented trying to attack with one of the implemented simulations to a proposal of modified fuzzy vaults that emerged within the CIC Cybersecurity Lab team, in order to test the hypothesis that such vaults could not be breached using the methods with which the attack simulations were built.
Keywords: Biometric cryptosystems, Polynomial Reconstruction, Cryptographic Attacks, Fuzzy Vault, Cross-Matching, Brute Force
Analyze the behavior of existing attacks on a cryptographic-biometric system through the generation of interaction diagrams of the entities involved, and build a simulation of an attack on the system, to determine the feasibility of using post-quantum schemes in the mitigation of such attacks.
This project has been 2 in two parts, the first one as a Research stay while being an undergraduate student, the second part was developed under the work done in the social service corresponding to my bachelor degree. The code of the realized implementations can be found in: Correlation Attack, Brute Force Attack, Automated Fuzzy Vault Implementation
The activities carried out within the social service in general terms were: